The Importance of Database Security
In today’s digital era, databases hold mission-critical data ranging from customer information to financial records. Protecting this data is not optional—it’s a necessity. With DBDesigner’s secure modeling tools, teams can implement strong access rules and encryption policies without manually coding complex security configurations.
“Over 70% of data breaches in 2024 were traced back to poor database security configurations.” – Global Data Protection Report
Why Security Defines Trust
- Data Integrity: Prevent unauthorized tampering
- Access Control: Restrict sensitive data to the right users
- Compliance: Meet GDPR, HIPAA, and SOC2 requirements
- Resilience: Defend against SQL injection and cyber threats
Core Security Layers
With visual database design, implementing layered protection becomes seamless:
- User Authentication: Strong passwords, MFA, and OAuth integration
- Role-Based Access: Grant permissions based on least privilege
- Data Encryption: Secure data at rest and in transit
- Audit Logging: Track who accessed what and when
- Network Hardening: Firewall and VPN for database endpoints
Real-World Security Application
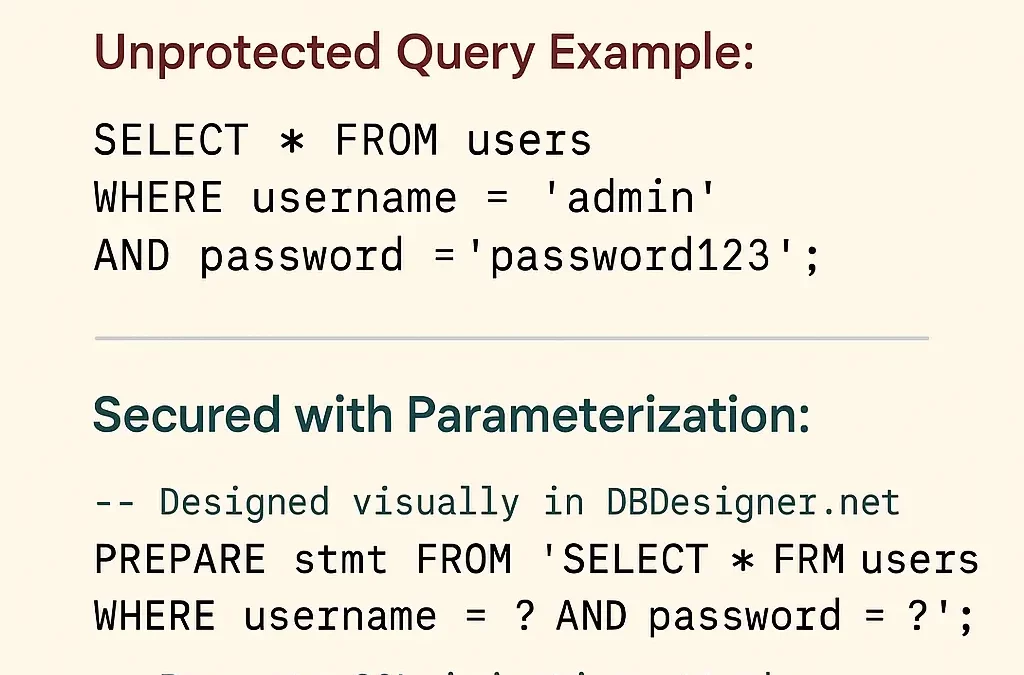
Unprotected Query Example:
SELECT * FROM users
WHERE username = 'admin'
AND password = 'password123';Secured with Parameterization:
-- Designed visually in DBDesigner
PREPARE stmt FROM 'SELECT * FROM users
WHERE username = ? AND password = ?';
-- Prevents SQL injection attacksSecurity Benefits
- Eliminates SQL injection risk
- Protects user credentials
- Ensures secure coding practices
Advanced Security Practices
- Data Masking: Hide sensitive fields from unauthorized roles
- Row-Level Security: Control access to individual rows
- AI Threat Detection: Use AI to identify abnormal queries
- Periodic Security Audits: Continuous compliance checks
Security Maintenance Best Practices
Monitoring
- Detect suspicious login attempts
- Review failed query logs
Patching
- Apply vendor security updates promptly
- Test patches in staging before production
Policy
- Define clear data access rules
- Regularly review user roles and privileges
Conclusion: Secure Your Data
Forward-looking teams integrate security by design to:
- Protect sensitive business information
- Maintain compliance with global regulations
- Build customer trust through robust security
Ready to Fortify Your Database?
Model Secure Databases Visually (With built-in encryption and access control support)
For Enterprises:
Implement enterprise-grade database security

Recent Comments